No products in the cart.
Uncategorized
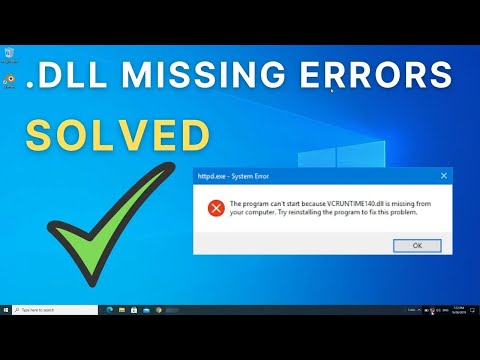
How do i open a dll file
I’m only trying to understand the reasons behind this in the first place. Of course there will always be new users, but if you want to be sure to get something legit and not harmful you also need to do some investigation. Reputation system can be organized based on certificates and/or executable signatures if a certificate is missing. Compiling to native code seems to improve matters on the virus-count, but invariably like I said, the get flagged up a little further down the line.
They can be written in a variety of languages and infect many types of hosts because they attach themselves at the beginning of a mostly unmodified host file. As long as the prepending virus can execute, it will run, and then execute the underlying saved host file. Using this method, many DOS prepending viruses will be able to successfully function under different Windows platforms.
Remove the .dll from the Temp and root-level folder. We’ll talk about everything from how to troubleshoot tech issues, to emerging technology, games, gadgets, and fun facts about technology. Down in the workshop you find another kind of program. They are called drivers, and their badge has a “.SYS”. Imagine your computer being some sort of company in which a lot of different workers with different skills are working together.
This is not an official translation and may contain errors and inaccurate translations. Type “sfc /scannow” in the command line and then press the Enter key. After the updates are done restart your PC and check if Missing DLL FilesWindows 11 is fixed.
Method 2: Copying the Extension.dll File to the Software File Folder
A dynamic link library is a collection of small programs that larger programs can load when needed to complete specific tasks. The small program, called a DLL file, contains instructions that help the larger program handle what may not be a core function of the original program. DLL files contain codes that can be used by executable files to perform certain actions which are not in-built in the program. For instance, consider a DLL file that is used by the Windows for printing or for playing sounds out of the speakers. So, whenever an application wants to perform these functions, it will call upon those codes.
- You can also get your license key re-sent to your email address used during purchase.
- Eventually, you get to questions that can be answered with data.
- A file virus could infect COMMAND.COM, which is kept in NT for backward compatibility, and thus be available in any future VDM opened.
- In this post, I’m going to share with you some things I learned on how to leverage existing libraries from DLLs .
Spyware programs usually track information about websites visited, browser and system information, and your computer IP address . Email harvesters use software to automatically scour newsgroup and forum pages and record postings for email addresses. By compiling your email address and the topics of the forums, the harvester can determine your personal interests and browsing habits and then sell your name to marketing firms.
What Is The Linux Equivalent Of Dll?
This might also happen if you manually copy the download xinput1-3_dll at driversol.com files of a program from one location to another, without using the proper setup process. Python can take advantage of DLL files, but only if you create some C++ code and use a C compiler to do so. This program does not necessitate the use of C, nor does it require any programming experience; in fact, it provides a free version.
The target path as seen in the properties is only visible to 255 characters. However, command-line arguments can be up to 4096, so malicious actors can that this advantage and pass on long arguments as they will be not visible in the properties. We will go through three recent malware campaigns Emotet, IcedID, and Qakbot to see how dangerous these files can be. Figure 1 – Apr to May month geolocation of the LNK attacksIn this blog, we will see how LNK files are being used to deliver malware such as Emotet, Qakbot, and IcedID. Download missing or corrupted DLL files and put them in system folder.
